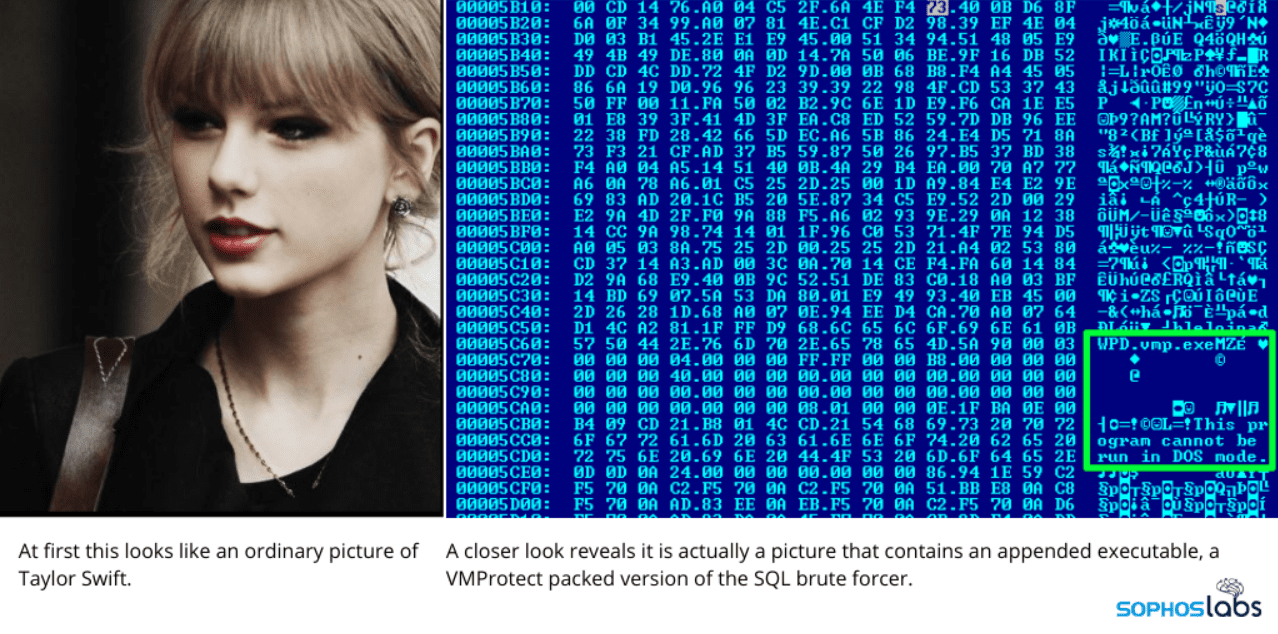
The operators of MyKingz, otherwise known as Smominru, DarkCloud, or Hexmen, are leveraging steganography, a technique that enables them to hide malicious files inside legitimate ones, according to UK cybersecurity firm Sophos.
In this instance, they are hiding a malicious EXE inside a legitimate JPEG image of Swift. “There’s a pretty good chance everyone who reads this story will have had some degree of interaction with a botnet we call MyKings (and others call DarkCloud or Smominru), whether you know it or not. For the past couple of years, this botnet has been a persistent source of nuisance-grade opportunistic attacks against the underpatched, low-hanging fruit of the internet. It’s probably knocking at your firewall right now. They certainly wouldn’t be the first,” Sophos warned. MyKingz was first spotted in the wild in 2017. It is now credited with being one of the largest cryptocurrency-mining malware available. The malware primarily focuses on Windows systems and features one of the most sophisticated scanning and infection mechanisms observed in botnets. It targets practically everything, including MySQL, MS-SQL, Telnet, ssh, IPC, WMI, Remote Desktop (RDP), and even the servers that run CCTV camera storage. During its first months, MyKingz reportedly infected over 525,000 Windows systems, netting more than $2.3 million worth of Monero (XMR). The countries with the highest population of infected hosts include: China, Taiwan, Russia, Brazil, USA, India, and Japan. It’s estimated that MyKingz infects approximately 4,700 new systems every day. The botnet‘s current income is about $300 per day, mostly due to a drop in Monero‘s exchange rate, Sophos added.