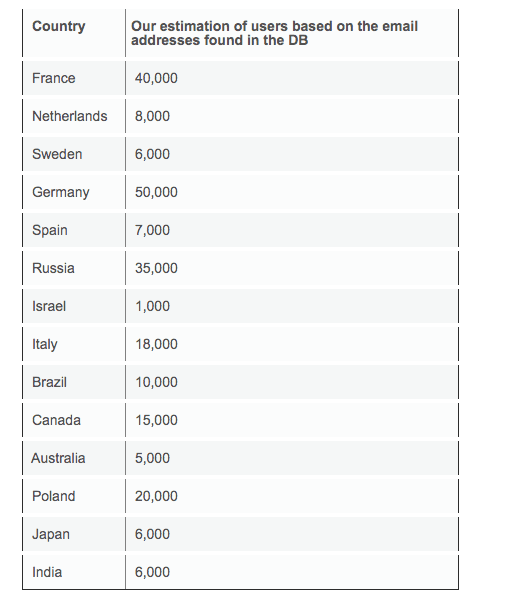
Security researchers from vpnMentor were able to exploit a kink in the adult-themed site to glean the personal data – including email addresses and countries of residence – of over 1 million users. The incident, the researchers argue, opens up Luscious users to a series of attacks, including phishing, doxing, and extortion. Among other details, the researchers were also able to view the users’ gender and activity on the platform, their uploads, comments, likes, and blog posts. All of these details were left out “completely unsecured and unencrypted,” the report notes. What’s particularly icky about the breach is that some email addresses contained users’ full names. Indeed, coupled with their activity, the researchers say a hacker could legitimately gain valuable insights into the how individuals use Luscious – and what type of content they’re into. Interestingly, a small number of users’ addresses were linked back to governmental and educational institutions from Brazil, Australia, Italy, Malaysia, and Australia. In total, the researchers identified less than a thousand .edu addresses and about a dozen .gov addresses. vpnMentor’s report suggests that a number of blog posts contained extremely personal stories, revolving around depressive episodes and other vulnerable details. The researchers note they first discovered the breach on August 15 and reported it to the site the next day. The vulnerability has since been fixed, according to their report. While it remains unclear if hackers took advantage of this security flaw in the wild, the researchers obtained the data of 1.195 million users. For the record, Luscious attracted more than 20 million visits last month, according to data from traffic monitor SimilarWeb. We’ve reached out to Luscious for further comment, and will update this piece accordingly if we hear back. Although unfortunate, this is hardly the first time researchers have found security holes in porn sites. Back in 2016, a data breach in xHamster popped 380,000 login details on the internet. In the same year, hackers dropped the details of 800,000 Brazzers accounts on the dark web. In the meantime, you can peruse vpnMentor’s full disclosure report by following the link here. Update 14:10 UTC, August 19, 2019: A Luscious spokesperson told TNW that “the data breach has already been secured, and we have put into place policies to not have it re-occur.” “We will be reaching out to any compromised users to warn them about the potential exposure of their private email addresses,” they added. Luscious did not clarify if the vulnerability has been exploited in the wild, but it did note that not all users had provided email addresses (since they’re not required when signing up).